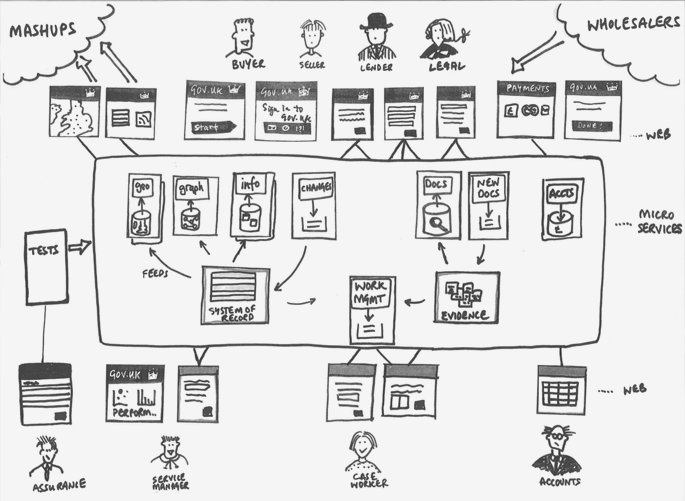
“One single vulnerability is all an attacker needs”
-Window Snyder
Mobile phones are becoming an efficient mode of communication and making life easier. New models and more advanced technology are introduced into the mobiles to meet the needs of people and make their life easier. With the ability to stay connected with people, pay bills online, storing data, taking pictures and many other irresistible features, the mobile phone has become an inevitable part in human lives.
As the different applications and features in a mobile phone make our life easier, it is also raising the risk of exposing our sensitive and confidential data to the hackers.
How do hackers cheat people to get their devices hacked?
The hackers are so much active and finding new ways to cheat people through a fake email, a fake web page etc. Especially, as people are in a state of fear due to this Covid-19, hackers are taking advantage of this situation. They use Covid-19 themes to create urgency and people unaware respond to this malware becoming victims of phishing and hacking. The scammers pretending to provide support and help by providing free meal coupons and such offers, often trick people to believe this is real. People unknowingly fall prey to this by clicking the malicious link and giving access to the personal information stored in their phones. Other sets of attackers persuade citizens to download malware by impersonating health organizations conveying important health information and tips.
Mobile malware, phishing, hacking is becoming common factors of threat in the mobile world. Protection of mobile phone data at personal and at the enterprise level has become very crucial.
How to protect your data in your mobile phones?
Bring self-awareness about security threats, training employees about the security measures, taking enough precaution steps are some good ways to protect the mobile phone data.
Popular brands have their own expert teams to protect their products and their users from attack. For example, Google’s Threat Analysis Group (TAG) is a group of experts that provide a solution to protect their products and their users from phishing and scams. They work continuously to identify new threats and scams in the market.
Various organizations provide several mobile security services such as Mobile Device Management (MDM), Mobile App Access (MAA), Data Leakage Protection (DLP), Identity Right Management (IRM).
Here are few recommended security practices everyone should follow at personal and at enterprise level:
- Implement robust authentication measures
- Ensure routine updates and data backup
- Block suspicious applications
- Continuous monitoring of connected devices
- Perform regular health checks
Let’s consider each of the security practice in detail.
1. How to implement robust authentication measures in mobile phones?
At personal level,
Set a screen lock (there are a number of ways to lock your smartphones based on the model of your phone), eliminate unwanted apps, block ads/tracking malware etc in your phone, keep notifications off the lock screen are some of the simple and common ways to secure your mobile phones.

Some more advanced mechanisms to provide secured passwords are providing pattern lock, setting a PIN number, and biometric authentication with fingerprint and face recognition. To make the authentication even stronger, one can combine these authentication methods along with multifactor authentication:
The different levels of authentication that can be applied on mobile devices are listed below:
Username Password authentication is sufficient where the apps are not very sensitive. This is a common form of authentication among social media apps.
Dual factor authentication
This method adds an additional layer of security making it harder for the intruder to get access to the mobile phone and its data. Here, PIN along with security token is used to authenticate users accessing the device.
Three factor authentication
Biometric factor along with this dual-factor authentication makes this authentication more secure to access the devices. The personal attributes of the user such as the voice or fingerprint are also used to authenticate the user in this method.
Geographical location tracking and device information
Geographical location tracking and device information can help prevent fraud by providing limited access to devices.
Behavioural analysis
Bigger enterprises also make use of technology connected to behavioural studies. It helps track any unusual user activities. If any different behaviour is noticed at the user end, they will be subjected to re-authentication. This behaviour also gets included in the Audit Analysis database for further monitoring and analysis.
The authentication mechanism that an enterprise adopts depends on their needs and ability to adopt security mechanisms. Some enterprise uses OTP to authenticate their user that works well for the enterprise needs. Many banking applications use OTP as a mean for ensuring security.
Other enterprises adopt PKI authentication which utilizes a private non-transferable encryption key stored as a hardware token. They are also recognized by government regulations.
2. Ensure routine updates and data backup

Ensure the updates are installed in mobile phones. Software updates for the mobile devices include the patches to the security holes for various security threats, so make sure to install the update as soon as they are available. Running an outdated or pirated version of OS could be more prone to mobile malware and malicious attacks.
Data backup is an essential security procedure that must happen at personal and at the enterprise level. The user data can be set for auto backup. How much and how often can be pre-defined.
At the enterprise level, based on how much data to back up and the budget available for data backup processes, they can choose an appropriate media like an external hard disk or NAS box with cloud back up for backing up their data. Other optical storage media like CD/DVD, Blu Ray etc can be considered as other cheaper alternatives, however, their life and capacity could be short.
3. Block suspicious applications

It is worth to check periodically what applications are given access to your device. The malicious apps may contain a piece of code that can extract personal details and other critical data. Before a download, always check the permissions of the app, the number of downloads, ratings, and reviews about the app. Do not download from third-party stores.
There is also good antivirus software available. Some are free, and some are paid but might provide better support. Based on your preferences, you may select a good one that meets your requirement.
4. Continuous monitoring of connected devices

Logging of activities at a various level can help to make access to mobile phone secure. Logging of text messages, social media activities, other web activity, application blocking etc to track any unusual activity can bring better security.
Protection can be made stronger at the enterprise level by using security services by various providers. For Example, AWS Security Hub, you can receive security threat alerts using services like GuardDuty for continuous threat detection.
5. Perform regular health checks

With emerging technologies and evolving security risks, the security aspects have become a huge challenge. Strong security solutions must be in place to identify vulnerabilities and an organization’s risk against real-world threats.
The more we are technology-dependent, the more we are prone to malware and cyber-attacks. It is mandatory that every individual is self-aware about phone security threats and preventive steps to protect their mobile phone data. Every employee at the enterprise level must be trained for security awareness.
Even if all the necessary steps to prevent the threat are in place, the security threat cannot be eliminated, however, it can be mitigated. There could still be attacks and losses, however, those losses could be controlled in a reasonable manner if we are well prepared. Security breaches, the violation to compliance law, data leakage etc. can cause severe damage to an organization’s reputation and trust among their users and business partners. So, it is very critical to adopt enough security measures to protect the data in smartphones and mobile applications.
Implementing effective security measures, making data protection practices a mandate, setting defined protocols for lost or stolen devices, spending money to bring security awareness among employees is a worthwhile investment and would benefit the organization in their long run.
“The only real security that a man have in this world is a reserve of knowledge, experience and ability”
Henry Ford